 100% Free Breach Search Engines That Show Your Actual Leaked Passwords
100% Free Breach Search Engines That Show Your Actual Leaked Passwords
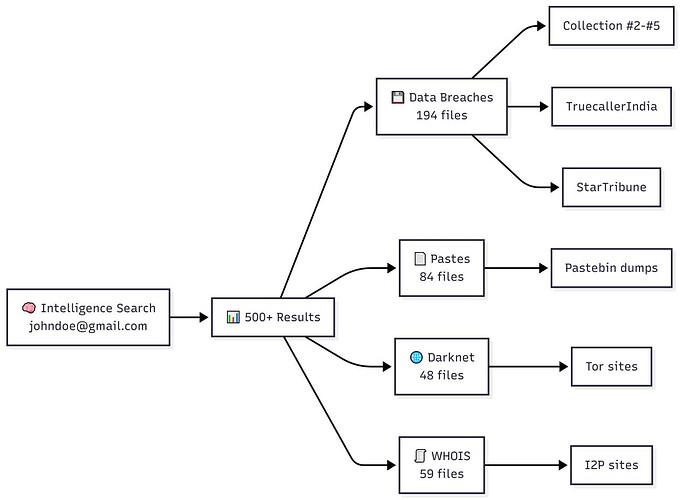
One-Line Flow: Type an email → see every breach, password, and dark corner of the internet where it appeared.
Why this matters:
Your email has been living a secret life across leaked databases, hacker forums, and malware logs. These tools let you see exactly what the bad guys already know — passwords, accounts, even browser autofill data. Same intel that costs thousands for corporations? Yours for free. Knowing your exposure = knowing what to fix before someone exploits it.
 What You’re Getting
What You’re Getting
Expand: The Big Picture
You’re about to access the same breach intelligence used by:
- Security researchers investigating hacks
- Journalists tracking data leaks
- Law enforcement finding compromised accounts
- Pentesters checking client exposure
Input: Email, username, phone, domain
Output: Every breach, paste, darknet mention, stealer log, and leaked password tied to it
No coding. No terminal. Just type and watch the results roll in.
 TIER 1: Instant Web Tools (Zero Setup)
TIER 1: Instant Web Tools (Zero Setup)
Type. Click. Results. That’s it.
 The Heavy Hitters (100% Free, Full Power)
The Heavy Hitters (100% Free, Full Power)
pwndb.com — The Stealer Log Monster
| What | Details |
|---|---|
| Records | 100+ Billion |
| Speciality | Infostealer malware logs |
| Shows | Full results |
| Limits | None |
| Account | Not needed |
This isn’t regular breach data. This is credentials harvested by actual malware (trojans, infostealers) from infected computers. The freshest, most dangerous type of leaked data.
Use it when: You want to know if your credentials were stolen by malware, not just leaked in a breach.
ProxyNova COMB — The Password Revealer
| What | Details |
|---|---|
| Database | COMB (Combination of Many Breaches) |
| Records | Billions |
| Shows | Actual passwords in cleartext |
| Account | Not needed |
| Limits | None |
Searches the legendary COMB database — the largest credential compilation ever assembled. Shows real passwords, not hashed garbage.
The move: Check your email → see your actual leaked passwords → change them immediately.
XposedOrNot — Open Source + Free API
| What | Details |
|---|---|
| Passwords indexed | 850 Million+ |
| API | Completely free, unlimited |
| Code | Fully open source |
| Features | Email breach check, password exposure, domain monitoring, risk scoring, alerts |
Key pages:
- Password checker: xposedornot.com/password
- API docs: xposedornot.com/api_doc
- GitHub: github.com/XposedOrNot
Why it’s different: Completely transparent. You can literally read the code. Plus free monitoring alerts.
DataBreach.com — Stealer Logs + Recent Breaches
| What | Details |
|---|---|
| Coverage | Stealer logs, traditional breaches, recent leaks |
| Notable | ALIEN TXTBASE (284M emails), 2025 breaches indexed fast |
| Shows | Breach timeline, source names, categories |
| Account | Not needed |
Direct links:
- All breaches: databreach.com/breach
- ALIEN TXTBASE: databreach.com/breach/alien-txtbase-stealer-logs-2025
Clean interface. Shows breach timeline. Updated fast when new leaks drop.
Have I Been Pwned — The OG (Now With Stealer Logs)
| What | Details |
|---|---|
| Breaches | 700+ indexed |
| NEW 2025 | Now searches stealer logs |
| Notable data | ALIEN TXTBASE (23B rows, 284M emails), Synthient (183M), Data Troll |
| Shows | Which specific websites your credentials were captured on |
| Alerts | Free email notifications |
The industry standard just got serious. Now tells you exactly which sites your email+password combo was entered into when malware captured it.
Pro tip: Subscribe for free alerts. Get notified the moment you appear in a new breach.
 Infostealer Detection
Infostealer Detection
Hudson Rock Free Tools — Were You Infected?
![]() hudsonrock.com/threat-intelligence-cybercrime-tools
hudsonrock.com/threat-intelligence-cybercrime-tools
| What | Details |
|---|---|
| Speciality | Infostealer infection checking |
| Malware tracked | RedLine, Lumma, Raccoon, Vidar, StealC |
| Check by | Domain, email, username, Android apps, technology stack |
| Background | Built by IDF 8200 cyber unit alumni |
Different from breach data: This checks if credentials were stolen by malware running on infected devices — corporate VPN access, webmail, cloud credentials. The stuff that leads to ransomware.
Use it when: You want to know if you (or your employees) got infected, not just breached.
 More Free Checkers
More Free Checkers
Expand: The Full Free List
| Platform | Link | What It Does |
|---|---|---|
| HEROIC Breach Scanner | heroic.com/breach-scan | Dark web + breach forums + stealer logs. Search by email, domain, IP, username, phone |
| LeakPeek | leakpeek.com | Shows leaked passwords. SMS/email monitoring alerts |
| BreachCheck.io | breachcheck.io | Dark web passwords + PII exposure |
| HackCheck.io | hackcheck.io | Data breach search engine |
| BreachDirectory.org | breachdirectory.org | Shows SHA-1 hash of password (crack at crackstation.net) |
| Scattered Secrets | scatteredsecrets.com | EU-based, actively cracks passwords from breaches |
| CyberNews | cybernews.com/personal-data-leak-check | 500GB+ database, instant check |
| Mozilla Monitor | monitor.mozilla.org | HIBP data with Mozilla privacy |
| F-Secure Checker | f-secure.com/identity-theft-checker | Report sent to your email |
| NPD Breach Check | npd.pentester.com | National Public Data breach (2.9B records) |
 TIER 2: Deep Search Engines
TIER 2: Deep Search Engines
When you need to dig deeper than basic breach checks.
Intelligence X (IntelX) — Darknet + Tor + I2P + Pastes
| What | Details |
|---|---|
| Records | 200+ Billion |
| Sources | Darknet (Tor/I2P), Pastebin, WHOIS, leaked databases, PDFs |
| Search by | Email, domain, IP, CIDR, Bitcoin address |
| Free tier | Limited but functional |
| Special | Free accounts for journalists/academics (apply) |
The tools page is gold: intelx.io/tools — opens 20+ search engines simultaneously. Free. No account.
Searches across:
- Email breach databases
- Username lookups
- Domain/IP info
- Social media (Facebook, Twitter, LinkedIn, Telegram, YouTube)
- Bitcoin addresses
- Phone numbers
- Hash lookups
- Google Analytics/AdSense IDs
Phonebook feature: phonebook.cz — Find all emails/subdomains/URLs for any domain (268B records)
OSINT Industries — Timeline Visualization
| What | Details |
|---|---|
| Sources | 1500+ |
| Search by | Email, phone, username, crypto wallets |
| Feature | Timeline visualization of activity |
Shows when accounts were created, when they appeared in breaches, activity patterns. Great for building a complete picture.
Venacus — 70TB of Raw Leak Data
| What | Details |
|---|---|
| Data | 70TB+ of leaked files |
| Search | ANY string — email, domain, password, anything |
| Features | MITRE ATT&CK mapping, cross-service search, bookmarks |
Not limited to emails. Search ANY text across massive leak archives. Like Google for breaches.
Features: venacus.com/features
LeakRadar — Fresh Stealer Logs Weekly
| What | Details |
|---|---|
| Records | 75 Billion+ plain-text credentials |
| Updated | 100M+ new credentials indexed weekly |
| Data | Stealer logs, combolists, database breaches, dark web dumps |
| Search by | URL, domain, username, password, email, TLD |
| Shows | Plain text passwords (not hashes) |
They publish weekly stats on how many credentials indexed. Search is free.
StealSeek — Stealer Log Hunting
Built specifically for hunting through stealer log data. Fresh credentials from infostealer malware.
IKnowYour.Dad — 86 Billion Records
| What | Details |
|---|---|
| Records | 86+ Billion |
| Databases | 3,877+ |
| Search by | Email, phone, username, password, documents |
Massive database. Searches everything.
CredenShow — Simple Breach Search
Data breach search engine. Enter email → get breach results with credential details.
 TIER 3: Username & Email Intelligence
TIER 3: Username & Email Intelligence
Find every account tied to a username or email across the internet.
 Username Enumeration
Username Enumeration
WhatsMyName.app — 640+ Platforms Instantly
| What | Details |
|---|---|
| Platforms checked | 640+ |
| Speed | Instant |
| Account | Not needed |
Type a username → see every platform where that username exists. Social media, forums, gaming, everything.
The data source: github.com/WebBreacher/WhatsMyName — open source JSON file that powers multiple tools.
More Username Tools
| Tool | Link | Platforms | Notes |
|---|---|---|---|
| Instant Username | instantusername.com | 100+ | Check username availability |
| Namechk | namechk.com | Domains + social | Username + domain availability |
| CheckUsernames | checkusernames.com | 500+ | Social network search |
| KnowEm | knowem.com | 500+ | Brand protection focus |
 Email Intelligence
Email Intelligence
Epieos — Silent Email Reconnaissance
| What | Details |
|---|---|
| Sites checked | 200+ |
| Method | Silent (target not notified) |
| Shows | Google account data, registered sites, social profiles |
| Free tier | Basic info |
| Paid | €29.99/month for full modules |
Why it’s different: Doesn’t ping the target. No false positives. Replaced the old Holehe module with proprietary engine that’s actually maintained.
More Email Tools
| Tool | Link | What It Does |
|---|---|---|
| Hunter.io | hunter.io | Find corporate email patterns. Domain → all employee emails |
| EmailRep | emailrep.io | Email reputation scoring |
| Email Format | email-format.com | Company email format patterns |
| That’s Them | thatsthem.com | Reverse email/phone/address lookup |
| Experte Email Finder | experte.com/email-finder | Name + domain → email guesses |
 TIER 4: CLI Tools (Extra Power)
TIER 4: CLI Tools (Extra Power)
For when you want to run searches locally or automate things.
h8mail — The Aggregator
pip install h8mail
h8mail -t [email protected]
Queries multiple services at once:
- Snusbase
- DeHashed
- LeakCheck
- HIBP
- IntelX
- HunterIO
- BreachDirectory
Supports local breach searching if you have the files.
GitHub: github.com/khast3x/h8mail
Sherlock — Username Hunter
pip install sherlock-project
sherlock username
Checks 400+ sites for username existence. The classic.
Maigret — Sherlock on Steroids
pip install maigret
maigret username
Enhanced Sherlock with profile data extraction. Pulls additional info from found profiles.
GitHub: github.com/soxoj/maigret
Holehe — Email Site Registration Checker
pip install holehe
holehe [email protected]
Checks which sites an email is registered on. Silent reconnaissance.
GitHub: github.com/megadose/holehe
Mosint — All-in-One Email OSINT
go install github.com/alpkeskin/mosint/v3/cmd/mosint@latest
mosint [email protected]
Combines: breach check, DNS lookup, social media, paste sites.
GitHub: github.com/alpkeskin/mosint
Linkook — Connected Account Discovery
git clone https://github.com/JackJuly/linkook
python linkook.py -u username
Finds connected accounts even with different usernames. Follows relationship links.
GitHub: github.com/JackJuly/linkook
LeakSearch — ProxyNova COMB Direct
git clone https://github.com/JoelGMSec/LeakSearch
python LeakSearch.py -d ProxyNova -k [email protected]
Query ProxyNova COMB directly from terminal. JSON/TXT export.
GitHub: github.com/JoelGMSec/LeakSearch
 TIER 5: Multi-Tool Portals
TIER 5: Multi-Tool Portals
One-stop shops that organize everything.
OSINT Framework
Visual map of 100+ OSINT tools organized by category. Click through the tree to find exactly what you need.
OSINT Combine Tools
Curated collection of working OSINT tools. Regularly updated.
IntelTechniques Tools
Michael Bazzell’s collection. Used by actual investigators.
Bellingcat Toolkit
Investigative journalism tools. Vetted and documented.
Awesome OSINT GitHub
![]() github.com/jivoi/awesome-osint
github.com/jivoi/awesome-osint
Massive curated list. If it exists, it’s probably here.
Awesome Hacker Search Engines
![]() github.com/edoardottt/awesome-hacker-search-engines
github.com/edoardottt/awesome-hacker-search-engines
Search engines for pentesting, OSINT, bug bounty. Organized by category.
 Investigation Workflows
Investigation Workflows
Copy-paste these for different scenarios.
Email Investigation Chain
Target: [email protected]
1. [HIBP] → Identify breaches + stealer log exposure
↓
2. [pwndb.com] → Check infostealer infection
↓
3. [ProxyNova COMB] → Get actual leaked passwords
↓
4. [Epieos] → Find registered sites + Google account data
↓
5. [DataBreach.com] → Recent breach exposure
↓
6. [IntelX] → Darknet/paste/Tor mentions
↓
7. [XposedOrNot] → Set up monitoring alerts
Username Investigation Chain
Target: username123
1. [WhatsMyName.app] → 640+ platform enumeration
↓
2. [Sherlock/Maigret] → Deep check + profile extraction
↓
3. [Linkook] → Find connected accounts (different usernames)
↓
4. If email found → Run email workflow above
↓
5. [IntelX Tools] → Multi-search social platforms
Domain/Company Investigation
Target: company.com
1. [Hunter.io] → Corporate email pattern discovery
↓
2. [Phonebook.cz] → All emails/subdomains/URLs (268B records)
↓
3. [Hudson Rock] → Employee infostealer exposure
↓
4. [IntelX] → Leaked documents, paste mentions
↓
5. For each email found → Run email workflow
 Quick Reference Tables
Quick Reference Tables
100% Free Platforms Comparison
| Platform | Stealer Logs | Shows Passwords | Unlimited | No Account |
|---|---|---|---|---|
| pwndb.com | ||||
| ProxyNova COMB | ||||
| DataBreach.com | ||||
| XposedOrNot | ||||
| HIBP | ||||
| HEROIC | ||||
| LeakPeek | ||||
| BreachDirectory.org | SHA-1 hash | |||
| Hudson Rock | ||||
| IntelX Tools | N/A | N/A | ||
| Venacus |
What Each Category Means
| Category | What It Is | Best Free Source |
|---|---|---|
| Data Breaches | Hacked company databases (LinkedIn, Adobe, etc.) | HIBP, DataBreach.com |
| Pastes | Text dumps on Pastebin and similar | IntelX, HIBP |
| Darknet | Tor/I2P hidden service mentions | IntelX, pwndb |
| Stealer Logs | Malware-harvested credentials from infected PCs | pwndb.com, Hudson Rock, LeakRadar |
| Combos/Lists | Compiled credential lists (email:password) | ProxyNova COMB |
| WHOIS | Domain registration records | IntelX Tools |
| Autofills | Browser-saved form data (names, addresses, cards) | Stealer log platforms |
 Understanding Stealer Logs
Understanding Stealer Logs
Why This Matters More Than Regular Breaches
Regular breach: Company gets hacked → their database leaks → your email+password from that one site.
Stealer log: Your actual computer (or someone else’s with your credentials) gets infected with malware → it harvests EVERYTHING:
- Every password saved in your browser
- Session cookies (bypasses 2FA)
- Autofill data (credit cards, addresses)
- Discord tokens, Telegram sessions
- Crypto wallet files
- Screenshots of your desktop
The infection sources:
- Pirated software/games with cracks
- “Free” premium tools
- Malicious downloads disguised as videos
- Phishing attachments
Major infostealers in 2025:
- Lumma (most dominant)
- RedLine
- Vidar
- Raccoon
- StealC
Where logs end up:
- Telegram channels (ALIEN TXTBASE, Moon Cloud, Observer Cloud)
- Dark web autoshops (Russian Market, Genesis Market)
- Criminal forums
The platforms in this guide index that data so you can check your exposure.
 Legal & Ethical
Legal & Ethical
Expand: Stay Safe
Always legal:
- Checking your own email/accounts
- Security research on your own systems
- Authorized penetration testing
These tools are used by:
- Law enforcement investigating crimes
- Security teams protecting companies
- Journalists investigating leaks
- Researchers studying breaches
- Individuals checking their own exposure
Don’t:
- Access accounts using found credentials
- Harass people with discovered information
- Use for unauthorized access to any system
Remember: Your email appearing in breaches doesn’t always mean YOU were hacked. It could be:
- Third-party services you registered on
- Companies that stored your data insecurely
- Marketing databases sold or leaked
- Contact lists from infected devices (not yours)
Knowing your exposure = knowing what to protect.
 Quick Start (5 Minutes)
Quick Start (5 Minutes)
Do This Right Now
Step 1: Go to haveibeenpwned.com → enter your main email → see breach list
Step 2: Go to proxynova.com/tools/comb → same email → see if actual passwords leaked
Step 3: Go to pwndb.com → check if you’re in stealer logs
Step 4: Go to hudsonrock.com/threat-intelligence-cybercrime-tools → check if your device was infected
Step 5: If any passwords found → change them everywhere you used them → enable 2FA
Step 6: Subscribe to HIBP alerts for ongoing monitoring
Total time: 5 minutes. Knowledge gained: priceless.
The difference between you and a hacker? They already checked your exposure. Now you can too.
Your data is already out there. These tools just show you what the bad guys already know.
Type your email. See the damage. Fix what matters.
 !
!